Identity and Access Management (IAM) is one of the first core concepts that we have to understand in our Amazon Web Services (AWS) learning journey. I have tried my best to explain the IAM concept with simple examples in this blog. I will cover the following points in this article.
- What is Identity and Access Management (IAM)?
- IAM user, group, and role.
- Hands-on lab: create an IAM user, group and role.
- IAM Policy and its types.
- IAM best practices.

1. What is Identity & Access Management (IAM)?
Let’s understand IAM with an analogy, we will consider an educational institute. Ever wondered why an educational institute issues an ID Card to every student, faculty, and staff? Right, the ID cards help the institute to have control over who can access the facilities offered by the institute. Your ID card acts as proof of you studying in that institute and thus using their facilities. In a very similar manner, AWS has an IAM service to help companies manage their identity in the cloud.
Identity and Access Management (IAM) is a framework that ensures the right people in your organization access a specific service they need to perform their job. Suppose you are working in an organization, every day when you enter the main entrance you have to either show your ID-Card to the security guard or swipe your login card. In this way, your organization ensures that you are the right person who can access the organization’s premises. And this is exactly how IAM works.
When you show your ID-Card, you prove that you are the right person. So you as a person are an IDENTITY. Further, upon showing your ID-Card to the security guard, he verifies whether the ID-Card Photo matches your face or not. Once verified successfully, you get ACCESS.
Throughout the process, you as a PERSON get ACCESS to the right premises. The purpose of an ID card is not limited to entering organization premises alone, it also serves as proof to access a lot of other services and facilities in the same organization. For example, some people can only use the account section, while some can only use Human Resources, and so on. There is a well-defined system of who can use what.
In the same way, Identity and Access Management (IAM) is a service in AWS that ensures the right person has access to the right thing. AWS IAM provides access control across all AWS services and resources. You can specify who can access which services and resources, and under which conditions. There is also the concept of IAM Policy which you can use to manage permissions to your workforce and systems to ensure least-privilege permissions.
I will discuss the IAM policy concept in further reading as mentioned earlier. Now let me take the IAM concept a step further and introduce you to three important concepts under the IAM service as below.
- Identification
- Authentication
- Authorization
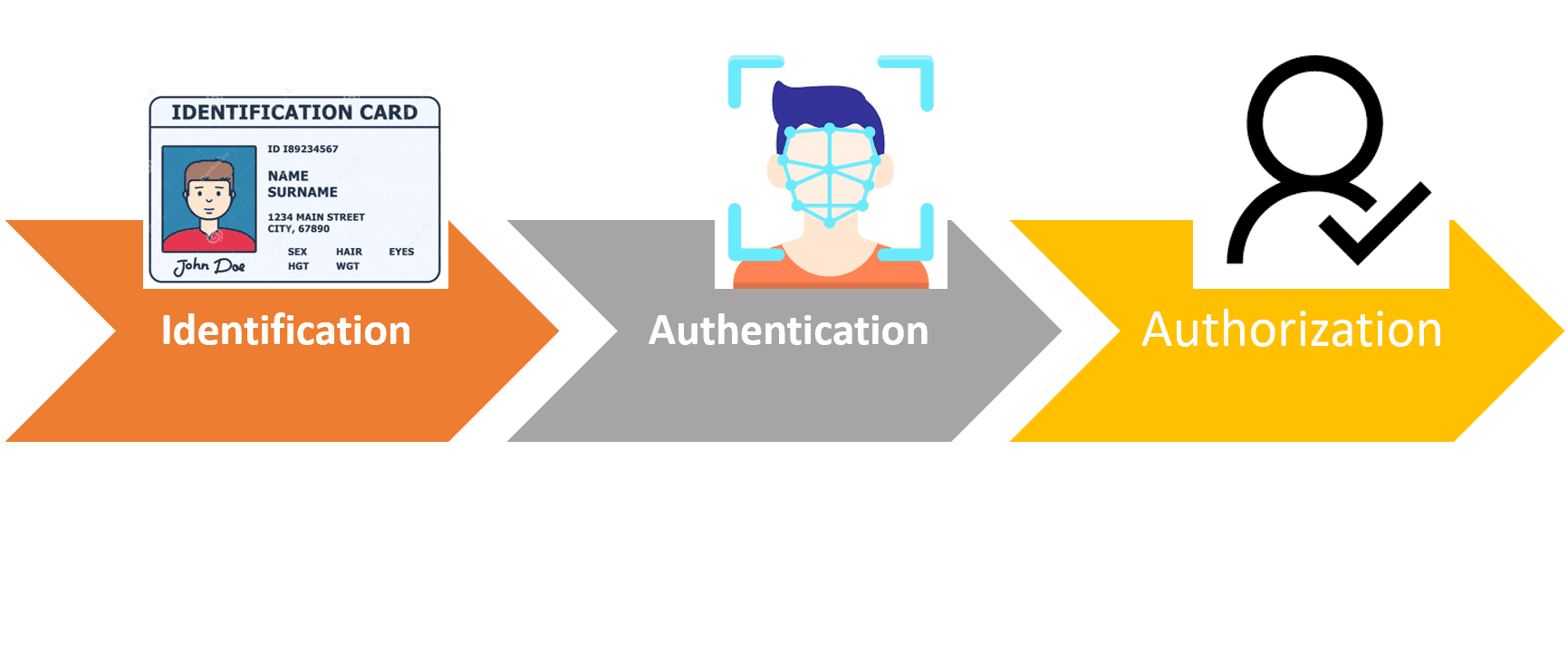
These three terms are closely related, but they are not the same. Let’s understand them.
- Identification is the ability to identify a user uniquely. It means, how a person or system can be identified. In the last example, you identify yourself with an ID-Card. Right? And that varies from system to system.
Consider logging into your bank account using your username and password. The bank website portal will allow you to sign in only if the username and password match the required criteria. In this scenario, your username and password become your identification factor. In this way, every user is uniquely identified and access to services and facilities is accordingly given.
- Authentication is the process of recognizing a user’s identity.
When you show your ID-Card to the security guard. He verifies your ID-Card photo with your face. That’s authentication. When you log in to your bank account, provide your username and Password. The banking backend system matches your username and password against the username and password stored in their database. The system makes sure you are given the right username and password. If you know the correct username and password, you are the owner of the account.
So if you have been given a unique identity, there has to be a system to recognize it every time you use your unique identity. And that process of recognizing the authenticity of your identity is known as authentication.
- Authorization is the process of giving someone permission to have access to something.
Once you are authorized, you can enter the office premises and can go to your office area. But you can’t go to the canteen kitchen, because you are not allowed or we can say you are not authorized to access the canteen kitchen area as per your job function.
Now, let’s understand Identity and Access Management (IAM) with respect to Amazon Web Services (AWS).
AWS IAM is an AWS service that helps an organization manage access to their AWS Account and Services for their organization’s people. It provides fine-grained access control across all AWS services. With fine-grained access, I mean to say you can specify who can access which services and resources and under what conditions. If you want person X to only access AWS EC2 service and person Y to access only S3 service. That’s completely possible with IAM.
Let’s continue the next sub-topic IAM user, group, and role in the next blog.

cfbr
I didn’t understand you.
Sir, cfbr is Commenting for better reach
Thank you Prashanth!
I am intereted in taking this up.
Great
I am intrested to learn
I am interested AWS
Very good teaching